15 Great, Free Privacy Downloads
One of the worst privacy invaders the world has ever seen is the Internet. When you surf, Web sites can find out where you've been and can gather other information about you. Trojan horses and spyware can snoop on you. Key loggers can capture your keystrokes as you type. Eavesdroppers can steal your passwords.
It doesn't have to be that way. The 15 downloads presented here can protect you. You'll find firewalls, password protectors, rootkit killers, trace cleaners, anonymity securers, and more. So check them out, and help yourself to a safer online experience. (Note that the 15 downloads we look at here don't include any antivirus and antispyware programs. We figured that we've covered those packages well enough elsewhere. So instead, we focus on tools you might not have heard about.)
Firewalls
A firewall is one of the most basic pieces of software you can get for protecting your privacy. Any decent firewall shields you from inbound snoopers, and the better ones also prevent sneaky software from sitting invisibly on your PC and making outbound connections to tell others about your activities. Comodo Firewall Pro
If you have Windows XP or Windows Vista, you have a firewall on your PC courtesy of Microsoft, so you may figure that you're perfectly safe. Wrong--the firewalls built into both of those operating systems have problems. The Windows XP firewall, for example, lacks outbound protection. And the Windows Vista firewall is exceedingly difficult to customize.
Vista Firewall Control
Windows Vista's firewall is better than the one built into Windows XP because it includes outbound protection as well as inbound protection. Outbound protection is vital, because Trojan horses and spyware often use silent outbound connections to do their damage. In addition, some surreptitious software uses invisible outbound connection from your PC to send out spam or malware without your knowling it.
Password Protection
Password theft is one of the greatest privacy dangers that an Internet user faces online. With the following downloads, you'll be able to keep your passwords private and yet still keep track of them
KeePass Password Safe
Most people have dozens of passwords that they use for Web sites, Web-based mail, ATMs, and more. They have become a fact of automated life. But it doesn't matter how much antivirus software and antimalware you use; if your password is stolen, you're in trouble.
KeePass Password Safe offers a simple way to keep track of all your passwords while keeping them safe. It lets you store all of your passwords in a lightweight, simple-to-use database, and it encrypts the database so that only you have access to it. You can lock it with a master password or with a file key.
KeyScrambler Personal
One of the biggest dangers you face online is theft of your user name and passwords for logging into commercial Web sites (such as banking and financial sites) and Web-based e-mail accounts. A criminal who steals that information could empty your bank account and use your e-mail address to pose as you.
This add-in to Internet Explorer and Firefox promises a simple way to keep you safe. As you type your password, KeyScrambler Personal scrambles it so that the information sent out over the Internet doesn't match what you type. That way, a lurking crook won't be able to steal your private information.
Cleaning Your Traces
As you surf, your web browser leaves traces of your travels on your PC. Web sites can look into some of those traces. And if other people use your PC, they can easily look at those traces as well. Luckily, there are tools that can get rid of the tracks you leave behind.
Another privacy problem relates to Microsoft Office documents containing private information (unbeknownst to the sender) that get sent out via e-mail. A download helps here, too, removing information that you don't want made public from the Office documents where it appears.
Free Internet Window Washer
Worried that Web sites may snoop on your Internet activities, or that someone else who uses your PC can see where you've been and what you've done? If so, you need an Internet washer--a tool that will delete your Internet Explorer browsing history, recently typed URLs, browsing history, and so on.
That's what Free Internet Window Washer does--for free. Click Wash Settings, then click Browsers, and then select what you want the program to clean. Back on the main screen, click Wash Now and the program will remove everything you've asked it to. If you prefer, click Test Now to see a preview of what the program will do.
CCleaner
Here's another great tool--and a longtime favorite of ours--for cleaning up all traces of your Internet activities. CCleaner cleans Internet Explorer and Firefox, of course, but also Adobe Acrobat, Adobe Flash Player, Google Toolbar, and Windows Media Player. It even picks up after major applications such as Microsoft Office, and it includes a Registry cleaner and an uninstaller.
SendShield
A lesser-known privacy problem may be among the most dangerous: hidden information in Microsoft Office documents that becomes exposed after the documents are made public.
This problem has struck some of the best-know enterprises in the world. In 2006, for example, Google publicly posted a PowerPoint presentation that contained notes disclosing highly sensitive financial projections to the world. Even worse, in 2003, Alistair Campbell, top communications aide to then-Prime Minister Tony Blair of the UK, released a Word document whose hidden information revealed that the British government had used plagiarized documents to justify its involvement in the Iraq war.
Rootkit and Malware Killers
Even the best antivirus and antispyware tools can't keep you completely safe. Rootkits often escape detection, and once they lodge on your PC, they give an outsider the power to take control of your system and help themselves to whatever private information they want. These two rootkit and malware killers, though, tip the odds in your favor.
F-Secure Blacklight Rootkit Eliminator
One dangerous type of malware that might infect your system is a rootkit. It hides deep in your system, using tricky techniques to shield itself from many antispyware, antimalware, and antivirus programs. With a rootkit in place, a malicious person can take complete control of your PC without your knowledge. Rootkits spread online in various ways, such as by riding along on another download.
HijackThis
If spyware or a Trojan horse slips past your defenses despite your best efforts, your best bet is to download HijackThis. It can help detect problems that other malware detectors can't find, and then will advise you about what to do.
Browsing Privacy and Security
Looking for multipurpose tools for protecting your privacy and security? The following three can help you surf anonymously, avoid trouble at wireless hot spots, and receive alerts about certain sites that may host malware designed to invade your privacy.
Tor
A surprising amount of information about you can be gathered as you surf the Web--including the operating system you use, the sites you've visited recently, your geographic location, and possibly your company (based on your IP address).
Hotspot Shield
Some of the most nefarious online dangers arise when you're away from your home or office: Wi-Fi hacking and snooping. In a hotspot at a public location, a bad guy can set up a sniffer to snoop on all the data sent by everyone nearby. The snoop can see all of the information you send and receive over the Internet, including your user names and passwords.
McAfee Site Advisor for Firefox
One of the best ways to protect your privacy is to avoid getting infected by malware. These days, most people get infected by downloading infected software or by visiting a Web site that installs malware without their knowledge. So you'd like to know whether a site you visit is likely to infect you directly or to harbor malware.
Firefox Add-Ons
One great thing about Firefox is the large number of add-ons available to improve your browsing experience. The options include plenty of privacy-related add-ons. These three are among the best.
NoScript
The Web is built on interactivity, but those wonderful interactive features can be used to attack and damage your PC. JavaScript, plug-ins, Java, and other kinds of scripts and code on Web sites are hazardous. But here's the problem: If you turn them off completely, you lose some of the nicest things on the Web; and if you keep them, you expose yourself to danger.
WOT
This Firefox add-in works in much the same way as the McAfee Site Advisor. WOT rates sites according to their privacy, security, and trustworthiness, from Excellent reputation to Very Poor reputation, and it displays an icon next to the Address Bar indicating how it rates a particular site. As you search, you'll be able to see the icon as well, so that you can decide before visiting a site whether you want to go there.
Secure Login
Little surprise that Secure Login provides a way to log you in to Web sites securely. It integrates with Firefox's password list--so when you visit a site, you can log in by clicking a button instead of having to type in your user name and password. Beyond that, Secure Login keeps your passwords safe in various ways. It stops any malicious JavaScript code from stealing your password, and it can block other password-stealing attacks, such as cross-site scripting (XSS) attacks.
Please refer below for more security tools posted by me:
Westpac gives away free security software
Personal Computer Security
MUST-HAVE Free Security Utilities
Turning FireFox To An Auditing Platform
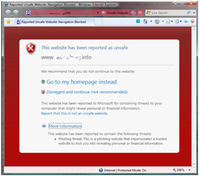 Firstly, Smartscreen Filter. Smartscreen filter is basically a virus scanner for websites. Any time you go to a dodgy site, RED ALERT! It'll allow you to continue, or give you the option to go to your homepage instead. You can also on-demand scan individual sites, much like you'd scan individual files with a virus scanner, and if you try to download dodgy files when a download site has been reported, it'll alert you too.
Firstly, Smartscreen Filter. Smartscreen filter is basically a virus scanner for websites. Any time you go to a dodgy site, RED ALERT! It'll allow you to continue, or give you the option to go to your homepage instead. You can also on-demand scan individual sites, much like you'd scan individual files with a virus scanner, and if you try to download dodgy files when a download site has been reported, it'll alert you too.![]()