Friday, May 30, 2008
Secure from Day One? Not Really!
Last week Nitesh and Billy Rios found a vulnerability in Safari that lets a remote attacker / malicious web site drop any file(s) they want on a users desktop if you're using Safari on Windows. The ability to drop a file on your desktop in and of is a security vulerability and bit scary for every day normal users.
Infact, Apple is not considering this as a security vulnerability. I read in ComputerWorld article that StopBadware.org, a group founded by Google Inc., Lenovo Group Ltd. and Sun Microsystems Inc., on Monday asked Apple to reconsider its refusal to address the flaw as a security problem.
Apple claims that user should enjoy worry-free web browsing on any computer. Apple engineers designed Safari to be secure from day one.
Now, i can understand clearly while Apple is not considering this vulnerability as Security issue:)
All i can suggest is if you are using Safari on Windows then Don't!
Wednesday, May 28, 2008
Compliance Testing
Its basically an audit of a system carried out against a known criterion. A compliance test may come in many different forms dependant on the request received but basically can be broken down into several different types:
- Operating Systems and Applications: A verification that an operating system and/or applications are configured appropriately to the companies needs and lockdown requirements, thus providing adequate and robust controls to ensure that the Confidentiality, Integrity and Availability of the system will not be affected in its normal day to day operation.
- Systems in development: A verification that the intended system under development meets the configuration and lockdown standards requested by the customer.
- Management of IT and Enterprise Architecture: A verification that the in-place IT management infrastructure encompassing all aspects of system support has been put in place. This is to ensure effective change control, audit, business continuity and security procedures etc. have been formulated, documented and put in place.
- Interconnection Policy: A verification that adequate security and business continuity controls governing the connection to other systems, be they Telecommunications, Intranets, Extranets and Internet etc. have been put in place, have been fully documented and correspond to the stated customer requirements.
The Australian Computer Emergency Response Team (AusCERT)
The AusCERT and the CERT® Coordination Center (CERT/CC) have produced the UNIX Security Checklist v3.0 which details steps to be taken to improve the security of most Unix Operating Systems. When carrying out compliance checks on most *nix systems I generally tend to quote from this lockdown and also the NSA guide when making recommendations to enhance system security.
This can be found here.
National Security Agency
The NSA has made publicly available a number of lockdown guides in one of its many initiatives to enhance awareness of the security issues effecting today's operating systems, applications etc. These guides I have found are generally easy to read, understand and in most cases give you a step-by-step guide to implement.
They can be found from here.
Microsoft Vista Hack
Roger Halbheer, shared a Microsoft Vista hack video. It is worth watching video but as Roger said, if you switch on Bitlocker, you are safe from this type of hacks. In my opinion, If hacker or bad guy have physical access then nothing is secure. They will try to do all nifty things.
Roger, also mentioned 10 Immutable Laws of Security, which is worth reading as well.
New Smart Phone Hack Could Expose Cell Network
Researchers to release hacking tool that gathers information about the cellular network to which a smart phone is connected.
Errata’s hack basically demonstrates how you can use information from the smart phone to get more access to the cell network than a user is supposed to have, Maynor says. And if Errata’s new tool were paired with the Universal Software Radio Peripheral (USRP), for example, he says, an attacker could hack the cell network itself.
Errata’s new hacking tool runs on an iPhone and gathers information about the cellular network to which the smart phone is connected.
Another danger, of course, would be an attacker exploiting the smart phone’s information to launch a malware attack that could disrupt the cell network.
Full article can be read here.
Tuesday, May 27, 2008
Vulnerability Management for Dummies
Grab a free Copy!
Qualys are offering free copies of the electronic version of Vulnerability Management for Dummies.
- Explains the critical need for vulnerability management
- Details the essential best-practice steps of a successful vulnerability management program
- Outlines the various vulnerability management solutions - including the advantages and disadvantages of each
- Highlights the award-winning QualysGuard vulnerability management solution
- Provides a ten point checklist for removing vulnerabilities from your key resources
The Price Of OverConfidence
Todd Davis (CEO of LifeLock) had his identity stolen. I was amused to read the article because LifeLock have 1 million dollar service gurantee. According to their website:
Our service guarantee is simple, but it is limited. We will pay up to $1,000,000 to cure the failure or defect in our service, per member, per lifetime for all incidents in the aggregate, regardless of circumstance.
Todd Davis, also claim:
His Social Security number is posted on his company website. Sometimes, too much publicity is not good for your product as well :)I'm Todd Davis, CEO of LifeLock, and yes, that’s my real social security number*. Identity theft is one of the fastest growing crimes in America, victimizing over 10 million people a year and costing billions of dollars. So why publish my social security number? Because I’m absolutely confident LifeLock is protecting my good name and personal information, just like it will yours. And we guarantee our service up to $1 million dollars."
Saturday, May 24, 2008
Is Security Research Ethical?
Answer to this question by another Security Expert....
I posted couple of days ago Face-Off: Is vulnerability research ethical?. Roger Halbheer has posted a very nice response to the debate by Bruce Schneier and Marcus Ranum.
The best part of Roger's response is:
Once you find a security vulnerability, what do you do with it? Do you do responsible or irresponsible disclosure?
As Roger said, I totally agree with his comments. It is not about security research, question is what we do after finding vulnerability? Finding security vulnerability is not a crime or unethical. What people do after that makes this unethical. If after finding vulnerability if we follow right responsible disclosure and company rewards the security researcher with dollors or whatever - that's approach is completely ethical to me. If after finding vulnerability if you follow irresponsible disclosure and sell the vulnerability in black market - that's approach is unethical.
As Roger said:
But to me, this is the wrong question: It is not so much about security research.
Thursday, May 22, 2008
Face-Off: Is vulnerability research ethical?
Security Experts Bruce Schneier & Marcus Ranum Offer Their Opposing Points of View
Of course, the topic of "vulnerability research" is really hot topic nowadays. Bruce Schneier and Marcus Ranum sound off in a Point-Counterpoint column on the ethics of vulnerability research. It's really interesting and worth reading debate between the two security experts.
This is the question which every security expert is looking for the answer, Is vulnerability research ethical?
Not only do we still have buffer overflows, I think it's safe to say there has not been a single category of vulnerabilities definitively eradicated. That's where proponents of vulnerability "research" make a basic mistake: if you want to improve things, you need to search for cures against categories of problems, not individual instances. In general, the state of vulnerability "research" has remained stuck at "look for one more bug in an important piece of software so I can collect my 15 seconds of fame, a 'thank you' note extorted from a vendor, and my cash bounty from the vulnerability market." That's not "research," that's just plain "search."I especially like that last line: "That's not 'research,' that's just plain 'search.'Every security expert will have different opinion to this question. It is really interesting to read the two security expert debating on this topic.
Tuesday, May 20, 2008
NetworkMiner
NetworkMiner is a Network Forensic Analysis Tool (NFAT) for Windows. NetworkMiner can be used as a passive network sniffer/packet capturing tool in order to detect operating systems, sessions, hostnames, open ports etc. without putting any traffic on the network. NetworkMiner can also parse PCAP files for off-line analysis and to regenerate/reassemble transmitted files and certificates from PCAP files.
The purpose of NetworkMiner is to collect data (such as forensic evidence) about hosts on the network rather than to collect data regarding the traffic on the network. The main view is host centric (information grouped per host) rather than packet centric (information showed as a list of packets/frames).NetworkMiner performs OS fingerprinting based on TCP SYN and SYN+ACK packet by using OS fingerprinting databases from p0f (by Michal Zalewski) and Ettercap (by Alberto Ornaghi and Marco Valleri). NetworkMiner can also perform OS fingerprinting based on DHCP packets (which usually are broadcast packets) by making use of the Satori (by Eric Kollmann) OS fingerprinting database from FingerBank. NetworkMiner also uses the MAC-vendor list from Nmap (by Fyodor).
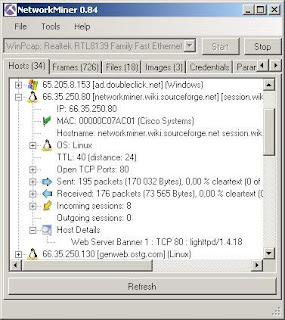
The newly released version 0.84 of NetworkMiner supports live sniffing of WLAN traffic (IEEE 802.11). This allows users to perform wireless network forensic analysis on any Windows machine with an AirPcap adapter installed. The RadioTap protocol as well as the Logical Link Control (LLC) protocol are also implemented in order to extract as much information as possible about the hosts communicating over a WLAN.
Monday, May 19, 2008
Spammers trying all possible ways
Here is the spam i received today:
From: "Mark Anthony" mark289@gmail.com
To: "Bronwyn"
Subject: Heyyyyyyy Bronwyn
Hey Bronwyn !
This is Mark , how r been? I havn't hear from you in a very long time! Mary
asked why didn't you come to our wedding? I was looking forward
to see you there then I tried to call you several times but it seem you
changed the number right ? is everything still okay with you ?
Here's some of the wedding pictures :
http://XX.XX.XXX.XX/mark-wedding/wedding.zip
Check it out and leave some comment for me . Miss u and hope to hear from
you soon.
Mark and Mary
Let analyse this:
1) This email came from gmail, which is hard for me to block or filter any messages from gmail. I receive legitimate emails from this domain.
2) My name is not Browyn for sure and i know few Mark so i cannot filter any messages which came from Mark or claim to be "Mark"
3) This email has a link which is asking me to download something in zip format. We all use .zip files everyday so it will not be clever of me to block any emails which has anything to do with .zip
Okay, forget for a little while that i know little about computers. I will just consider myself as a normal computer user. Now i have received this email i will have following reactions:
1) Oh i have excellent spam protection. This email is from gmail. I know gmail has very good security. It must be one of my friend.
2) My name is not Browyne but maybe Mark was forwarding email to Browyn and he forwarded to me? Maybe :S
3) I know alot of Mark. It's so nice of him to send me his wedding pictures let me download and view them.
I think majority of the people way think in a similar way i thought second time.
Conclusion:
We all know they are very smart people out there. They are working 24 / 7 days to beat spam filters. They will try all the possible ways to get through spam filters and reach your inbox. My suggestion would be if you don't know the person or doesn't recall his name - DON'T CLICK ON ANY UNTRUSTED LINKS.
Friday, May 16, 2008
Some tips to Protect Yourself on MSN Messenger
One of my best mate Chris asked me to blog something about MSN messenger hack protection.
MSN Messenger is one of the most common instant messaging programs that are used across the world. With over millions of people signing up a year, it is no surprise that viruses and other forms of malware get passed through this software. In fact, there has recently been a large increase with malware received through programs just like MSN Messenger. Nevertheless, there are many simple solutions for you to use that can protect you from and harmful content.
Contacts
The people you talk to on MSN Messenger are likely to be people that you know in real life. This is perfectly safe, and you will most probably never have to worry about any danger coming from them. Any time a contact adds you on MSN, you should receive a pop up box that appears when you log in. By looking at the email that has added you, you should be able to tell whether you know this person or not.
Unfortunately, some emails do not reveal the name of the person who owns that particular email address. In this case, if you feel any suspicion about the email address that has added you, uncheck the box that says "Add this person to my contact list". By doing this, when the new contact messages you, he or she will not be able to see your display picture, and you will not be able to see his or her nickname. Until you can be sure that the person who added you is someone you know in real life, keep them off your contact list to prevent them from seeing some of your information. Once you have verified that the contact is in fact someone you know in real life, you can add them to your contact list by click that "Add to contact list" button towards to the top of the conversation window when talking to them.
Some email addresses you can immediately block. MSN staff will NEVER add you as a contact on MSN. To contact you, they will email you via Hotmail. Email addresses such as updater@hotmail.com. Email addresses such as these are known as phishing scams. By pretending to be some sort of administrator, they will most likely try to direct you to a harmful site or coerce you into telling them your password. You can block these kinds of email before ever adding them to your contact list. This will ensure your safety.
Emoticons
Emoticons are a lot of fun to use. You can even create your own emoticons and show them to other friends. However, there is some way to store a virus on an emoticon. When someone displays an emoticon to you, you have to download the picture just like any other normal picture. If that person were to attach some sort of malware to that picture, you may effectively 'download' a virus without even knowing it. There is a way to prevent this though.
On the main MSN window, click tools
Go to options
Go under Messages
On the right, uncheck the box that says 'Show custom emoticons'
Click ok
By doing so, you can no longer send or receive custom emoticons. As much as a loss as this may be to you, you make yourself much safer. It is well worth the loss to disable custom emoticons.
Display Pictures
There have been isolated instances of malware being transmitted with display pictures. Since you are free to use any display picture you choose, hackers may attach some malware along with the picture. When downloading this picture to view it, you may accidentally download the malware as well. Although this is rare, there is a way to disable it. Only do it if you are not much computer savvy.
On the main MSN window, click tools
Go to options
Go under Personal
Uncheck the box that says 'Show my display picture and allow others to see it'
Though display pictures are quite important, you may want to disable this if you regularly talk to people you do not know in real life.
File Transfer
One of the most common ways of being infected by malware over an Instant Messaging program is by the transferring of programs. You should never accept any files from someone that you do not know personally. If you really do need to accept a file from someone, you can help to protect yourself by scanning it.
On the main MSN window, click tools
Go to options
Go under File Transfer
Check 'scan files for viruses using:'
Click the browse button
Find your Antivirus software and double click it
Click ok
You will now use you antivirus program to scan any files that you accept. This will help prevent any harmful programs to infect your computer.
Hacked MSNs
From time to time you are bound to have a friend that had his/her MSN hacked. When this occurs, immediately block that person until your friend tells you that they have regained control over their account.
Unfortunately, you do not always know when your friend's MSN has been taken over. When this occurs, the hacker may try to infect your computer as well. By following these steps you should be safe:
If a conversation is started by them wanting to transfer a file, DO NOT ACCEPT IT.
Do NOT click any links until you talk to them, and they reply
Most of the time, it is not the hacker themselves talking to you. It is an automated message to you.
When they start to talk to you, reply and ask them a question or two. If they do not answer, do not click any links or accept any files they may want to send. It is unlikely that they will leave the computer right after trying to contact you. Even if their MSN was not hacked, they can always resend the file.
Wednesday, May 14, 2008
Turning FireFox To An Auditing Platform
Auditing exTensions for FireFox
Firefox offers nowadays much more than browsing the web, but auditing the targets. A lot of extensions (and much more to come) exist and lead security auditors to reveal hidden or misc information undetected by traditional application scanners.
The fact is that firefox and its extensions act as an in-between layer collecting all traffic sent and received from the targets.
Here are some useful extensions I am aware of which I use in my regular security testing.
FoxyProxy: FoxyProxy is an advanced proxy management tool that completely replaces Firefox’s proxy configuration. It offers more features than SwitchProxy, ProxyButton, QuickProxy, xyzproxy, ProxyTex, etc
HeaderMonitor: This is Firefox extension for display on statusbar panel any HTTP response header of top level document returned by a web server. Example: Server (by default), Content-Encoding, Content-Type, X-Powered-By and others.
HostIP.info Geolocation Plugin: Displays Geolocation information for a website using hostip.info data. Works with all versions of Firefox.
QArchive.org web files checker: llowing people to check web files for any malware (viruses, trojans, worms, adware, spyware and other unwanted things) inclusions.
Bibirmer Toolbar: An all-in-one extension. But auditors need to play with the toolbox. It includes ( WhoIs, DNS Report, Geolocation , Traceroute , Ping ). Very useful for information
gathering phase.
View Dependencies: View Dependencies adds a tab to the "page info" window, in which it lists all the files which were loaded to show the current page. (useful for a spidering technique)
Active Whois plugin for Firefox: Starting Active Whois to get details about any Web site owner and its host server.
SwitchProxy Tool: SwitchProxy lets you manage and switch between multiple proxy configurations quickly and easily. You can also use it as an anonymizer to protect your computer from prying eyes
RefControl: Control what gets sent as the HTTP Referer on a per-site basis.
Fire Encrypter: FireEncrypter is an Firefox extension which gives you encryption/decryption and hashing functionalities right from your Firefox browser, mostly useful for developers or for education & fun.
Shazou: The product called Shazou (pronounced Shazoo it is Japanese for mapping) enables the user with one-click to map and geo-locate any website they are currently viewing.
JSView: The ’view page source’ menu item now opens files based on the behavior you choose in the jsview options. This allows you to open the source code of any web page in a new tab or in an external editor.
View Cookies: It adds a tab to the Page Info dialog box, which shows the cookies of the current webpage. This is interesing for developers, privacy-concious users and others.
Tamper Data: Use tamperdata to view and modify HTTP/HTTPS headers and post parameters.
Cert Viewer Plus: Adds two options to the certificate viewer in Firefox or Thunderbird: an X.509 certificate can either be displayed in PEM format (Base64/RFC 1421, opens in a new window) or saved to a file (in PEM or DER format - and PKCS#7 provided that the respective patch has been applied - cf.
refspoof: Easy to pretend to origin from a site by overriding the url referrer (in a http request). — it incorporates this feature by using the pseudo-protocol spoof:// .. thus it’s possible to store the information in a "hyperlink" - that can be used in any context .. like html pages or bookmarks
SpiderZilla: Spiderzilla is an easy-to-use website mirror utility, based on Httrack from www.httrack.com.
HackBar: This toolbar will help you in testing sql injections, XSS holes and site security. It is NOT a tool for executing standard exploits and it will NOT learn you how to hack a site. Its main purpose is to help a developer do security audits on his code.
People Search and Public Record Toolbar: This Firefox extension is a handy menu tool for investigators, reporters, legal professionals, real estate agents, online researchers and anyone interested in doing their own basic people searches and public record lookups as well as background research.
Tuesday, May 13, 2008
Security Vulnerabilities and Exploits
One of the difficulties faced by IT security professionals is keeping up with the latest security vulnerabilities in operating systems, databases, and applications.
If an attacker knows a vulnerability and you don’t, your may not be able to effectively defend against the new vulnerability. This is especially true of applications which are accessible from the Internet.
Many sources of security news document vulnerabilities only in general terms. This often does not give the security administrator enough information to effectively defend their systems from attack.
As a result, most security professionals keep up-to-date by attempting to monitor the hacking community. The hacking community, however, consists of tens of thousands of different individual and groups working in a decentralized and unorganized manner.
As such, it is difficult or impossible for any single security professional to keep up with new vulnerabilities discovered by the entire hacking community.
Milw0rm.com is an excellent resource to help with that problem. Milw0rm.com lists vulnerabilities, along with exploits and shellcode. These are organized by platform and by type of access required. I support and in favour of websites like that because they give out exploits and vulnerabilities details openly rather then under table and taking money for it - which makes it unethical.
Milw0rm.com is an excellent addition to resources such as Open Source Vulnerability Database, The National Vulnerability Database, and Exploit Tree.
Sunday, May 11, 2008
Cyber Ethical Issues
Last year, Roger Halbheer, blogged couple of times about WabiSabiLabi. Roger questioned the world in his post that whether it is ethical to sell the exploits openly to the highest bidder?
In my opinion i think it is completely unethical to sell the exploits openly. WabiSabiLabi might be supporting the security researchers in rewarding them for their creative work but are they selling the exploits to the right people? The people who are buying the exploits might not have right motive? They might target the companies who are vulnerable to that exploit (most likely they will be vulnerable) and cause huge financial loss? These were the questions which Roger were looking answers for last year.
On WabiSabiLabi website they have mention:
Wabi-sabi is the perfect term to represent the implicit imperfection of the IT security, as well as the scope of our project, which is to contribute to its improvement. This goal is achieved by completely re-designing the traditional security research cycle, introducing for the first time ever a market-driven approach to correctly value the security researchers contributions.
I really don't understand are they really achieving their goal by completely re-designing the traditional security research cycle, ethnically or unethically?
Recently, i came across of a similar website called: Astalavista. According to the website:
The ASTALAVISTA hacking & security community is the largest IT security community in the world. It’s a platform for both IT specialists and novices, and anyone interested in expanding and updating their knowledge regarding IT security and hacking.
They are offering paid subscription for the following prices:
- 6 months - $39.95
- 24 months - $99.95
- Lifetime membership - $199.95
Okay, according to them here are the benefits for becoming the member:
- The latest tools
- Unpublished documentation
- The largest security archive on the Internet
- Zero-Days Exploits
- Live Hacker Reports
- E-Books
- Tutorials
- Source Codes
- Tips and Tricks
- Hosted Forums
- War Games Servers
..and still many more..
They claim that their members include IT security specialists and IT representatives at multinational companies like IBM, Microsoft and PWC.
Now i have the similar question which Roger Halbheer asked last year. Is these types of security forums are ethical and beneficial for security community? Is ethical, to pay some hackers and get hold of Zero-Day exploits?
If really representives from companies like Microsoft, IBM and PWC companies are supporting such forums then i personally think that we are not fighting with bad guys infact we are working with them together.
Friday, May 9, 2008
Hacker's Choice
According to DarkReading:
It takes the average attacker less than 10 seconds to hack in and out of a database -- hardly enough time for the database administrator even notice the intruder. So it’s no surprise that many database attacks go unnoticed by organizations until long after the data has been compromised.
Hackers' top six database attacks:
1. Brute-force (or not) cracking of weak or default usernames/passwords
2. Privilege escalation
3. Exploiting unused and unnecessary database services and functionality
4. Targeting unpatched database vulnerabilities
5. SQL injection
6. Stolen backup (unencrypted) tapes
To read full article please click here.
Wednesday, May 7, 2008
Yahoo ads accidentally serve up malware
Whoops! That's what Yahoo is saying, or at least should be saying, after it was discovered that some of their banner ads have been serving up malware. While nobody would assume that Yahoo would endorse peddling nasty software to people’s machines, the article asserts that the technical teams at Yahoo might not even be aware that there is a problem. It seems that certain banner ads are hosted on or are contacting servers that produce pop-ups eerily similar to Windows dialogs. We've all seen them before, but most of us are wise enough to know that Windows dialogs urging you to fix a problem now (and possibly pay for it) are bad news.
Unfortunately for Yahoo, and just about any company that relies on ad revenue, the multitude of ad-serving companies in existence makes it hard to track each and every individual ad. Hopefully they will track down the culprits involved regardless, before too many users find themselves with spyware.
To read full article please click here.
Tuesday, May 6, 2008
Microsoft Vista - Secure OS Not Failure
Vista's 11 Pillars of Failure - Interesting, Let's have a look!
According to PCmag's John C. Dvorak Microsoft Vista has 11 Pillars of Failure. I am quoting Vista's 11 Pillars of Failure headings from the article and putting my comments. The full article can be read from here.
- Market Confusion: I don't think there was any Market confusion at the time of Vista release. I do agree with you guys that Microsoft is not big in marketing there products but still they didn't left any stone unturned.
- Code Size: Oh, Come on! Yes, Vista has too big code size. But, it's secure and has less patches then other operating system.
- Missing Components: Microsoft is considering an update of WinFS for Vista. Don't know, what's happening in this field!
- Laptop-battery life drain: Now, laptop-battery will decide the fate of Operating System? That's funny!
- HHD fiasco: I think people are still not fully aware of this one. I suppose, HD industry has started taking initiative in this field for some time now.
- Bogus Vista-capable stickers: I haven't experience or heard anything like that. Have you?
- Missing drivers: Well, initially there were problems with the drivers. I didn't see any issues lately.
- Conflicting advice: I think author didn't do his research properly. Microsoft did launch dedicated Upgrade Advisor. Please refer here.
- XP mania: I agree, people are still in love with Microsoft XP. I will say again, Microsoft Vista focused more on security and advance features then XP.
- Mediocre rollout: I slightly disagree with this one. Microsoft, i know little that they are not best in marketing but they did their best in providing the best roll out solution for Microsoft Vista.
- Performance: Yes, i agree Microsoft Vista is slow and have performance issues. But, if we use good and high speed hardware. Performance is not too bad. After all, Microsoft Vista is far more secured and better Operating System available in market today.
Conclusion: Well, I think author hasn't done proper research before publishing this article. I personally think, Microsoft Vista is the most secure OS available in market to date. According to Jeff Jones, Windows Vista One Year Vulnerability Report, it clearly shows that Vista has fewer patch release then other Operating Systems. I agree, Vista hasn't done well in market yet. In future, i think this will change as people will get more security awareness.
Paypal Boosts security
In efforts to boost security, Paypal, one of the premier internet online payment providers is moving to block users who use older browsers to prevent weaknesses that these browsers possess. They have found that many users online still use old Microsoft IE 3.0 and 4.0 which have ended their support life a long time ago hence they do not have the needed updated security updates that are necessary to conduct safe and secure online transactions with regards to payments and other related business.
Paypal has had a lot of bad publicity with regards to phishing and infiltration where people intercept and go on fake bidding sprees just to get at the vital financial information that people usually share over the network. In hopes of boosting security, they will be using script detection to begin blocking users and that they do apologize for all the inconvenience this may cause the millions of users who may be affected by their move.
Please refer to this article on NewsFactor website for further details.
Monday, May 5, 2008
The Post-American World
This article from Fareed Zakaria of Newsweek is long but an absolute must read. The article starts off by talking about the relative decline of America with respect to the rest of the world but it goes on to put things in proper context.
It's true China is booming, Russia is growing more assertive, terrorism is a threat.
But if America is losing the ability to dictate to this new world, it has not lost the
ability to lead.
Friday, May 2, 2008
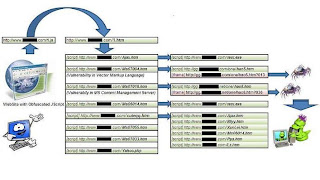
Malicious IFRAMES Attack
This graph is an example of the infection process that takes place from the moment when a user accesses a legitimate website that has been modified until the possible infection is effective.
Just incase, you want to know - "What is Iframe?"
An IFRAME is an HTML element whose content is determined by another file (usually an html file, but any valid web page URL). The content of that URL is displayed inside an inline frame, which is basically a rectangle.
An iframe element displays content, including forms, images, multimedia, other frames, tables, etc. It is very important to understand that the only way to assign content to an iframe is to assign a URL using the src attribute. Whatever content is displayable at the referenced URL will in turn be displayed inside the iframe.
If you like good description and understanding about an IFRAME please refer here. Dancho Danchev has done an excellent research about an IFRAME attack please refer to his post "Embedding Malicious IFRAMEs".
Session Hijacking
A great hacking tools created by yehg community, its called jhijack. A simple Java Fuzzer mainly used for numeric session hijacking and parameter enumeration.
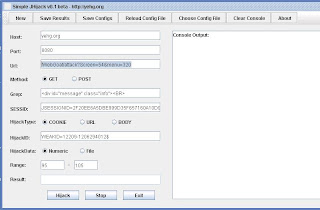
We can see from the snap shot that this tools can hijack with a several range session ID, just put the “$” variable and set the range below it. We can download this tools here and we can also download the flash based tutorial from here.