Friday, December 19, 2008
Google implant in your brain
After the evident monopoly of google over the world wide web, What's next? You may find it funny, but this is the dream of Google Founder.
I was surprised when I heard Google is making a micro chip that can be transplanted into human brain. Wouldn't it be like a science fiction if that is achieved?
Whenever you need some information you close your eyes and wander into the infinite virtual world. That would be amazing, We will probably hear that soon.
In the meantime i think it will also take care of the memory problem. I keep forgetting what was i talking about. May be i could bookmark my thoughts, save it, edit it or may be just erase it- if i don't like it.
People might talk about you think fast. What do you have - Xeon 100+? I'll need to upgrade my RAM. Haha, for the time being let's just reboot!
Wednesday, December 17, 2008
Lawyer used Facebook for his case, so be careful
It could be legal history in the making but it is certainly something that will make at least a few dread the Facebook. Defaulters - many that are there thanks to one of the world’s worst credit crisis - can only pray this does not become a trend but Canberra lawyers have won the right to serve legally binding court documents by posting them on defendants' Facebook sites.
Email and even mobile phone text messages have been used before to serve court notices, but in a historic ruling, the Australian Capital Territory Supreme Court ruled last week that lawyers could use the social networking site to serve court notices.
I qoute from the article:
''The Facebook profiles showed the defendants' dates of birth, email addresses and friend lists and the co-defendants were friends with one another,'' a spokesman for lending company MKM Capital said.
This information was enough to satisfy the court that Facebook was a sufficient method of communicating with the defendants
Lawyers Meyer Vandenberg, acting for lending company, applied to Master David Harper of the Supreme Court last week to use the popular internet site to serve notice of a judgment on two borrowers who had defaulted on a loan.
Carmel Rita Corbo and Gordon Kingsley Maxwell Poyser failed to keep up the repayments on $150,000 they borrowed from MKM last year to refinance the mortgage on their Kambah townhouse.
MKM applied to the courts through Meyer Vandenberg for a judgment for the loan amount and for possession of the defendants' house after the couple failed to appear in court to defend the action.
A default judgment was granted on October 31 leaving MKM with the task of finding the defendants and serving them with the papers.
Meyer Vandenberg hired private investigators to serve the judgment on the couple and advertised it in The Canberra Times. But after 11 failed attempts to find the couple at their Wyselaskie Circuit home between November 8 and December 6, the lawyers tried a change of tack. Lawyers Mark McCormack and Jason Oliver convinced the court the Facebook profiles for the defendants were those of Ms Corbo and Mr Poyser.
Tuesday, December 16, 2008
12 Most Vulnerable Apps
Mozilla’s flagship Firefox browser has earned the dubious title of the most vulnerable software program running on the Windows platform.
According to application whitelisting vendor Bit9, Firefox topped the list of 12 widely deployed desktop applications that suffered through critical security vulnerabilities in 2008. These flaws exposed millions of Windows users to remote code execution attacks.
The other applications on the list are all well-known and range from browsers to media players, to VOIP chat and anti-virus software programs. Here’s Bit9’s dirty dozen:
- Mozilla Firefox: In 2008, Mozilla patched 10 vulnerabilities that could be used by remote attackers to execute arbitrary code via buffer overflow, malformed URI links, documents, JavaScript and third party tools.
- Adobe Flash and Adobe Acrobat: Bit9 listed 14 flaws patched this year that exposed desktops of arbitrary remote code execution via buffer overflow,“input validation issues” and malformed parameters.
- EMC VMware Player,Workstation and other products: A total of 10 bugs introduced risks ranging from privilege escalation via directory traversal, ActiveX buffer overflows leading to arbitrary code execution and denial of service.
- Sun Java JDK and JRE, Sun Java Runtime Environment (JRE):
Inability to prevent execution of applets on older JRE release could allow remote attackers to exploit vulnerabilities of these older releases. Buffer overflows allowing creation, deletion and execution of arbitrary files via untrusted applications. 10 patched vulnerabilities listed
- Apple QuickTime, Safari and iTunes: In QuickTime, the list includes nine vulnerabilities that allow remote attackers to execute arbitrary code via buffer overflow, or cause a denial of service (heap corruption and application crash) involving malformed media files, media links and third party codecs. The Safari for Windows browser was haunted by three flaws that could be lead to arbitrary code execution and denial of service involving JavaScript arrays that trigger memory corruption. Apple’s iTunes software was susceptible to a remote improper update verification that allowed man-in-the-middle attacks to execute arbitrary code via a Trojan horse update.
- Symantec Norton products (all flavors 2006 to 2008): Stack-based buffer overflow in the AutoFix Support Tool ActiveX exposed Windows users to arbitrary code execution.
- Trend Micro OfficeScan: A total of four stack-based buffer overflows that opened doors for remote attackers to execute arbitrary code.
- Citrix Products: Privilege escalation in DNE via specially crafted interface requests affects Cisco VPN Client, Blue Coat WinProxy, SafeNet SoftRemote and HighAssurance Remote. Search path vulnerability, and buffer overflow lead to arbitrary code execution.
- Aurigma Image Uploader, Lycos FileUploader: Remote attackers can perform remote code execution via long extended image information.
- Skype: Improper check of dangerous extensions allows user-assisted remote attackers to bypass warning dialogs.Cross-zone scripting vulnerability allows remote attackers to inject script via Internet Explorer web control.
- Yahoo Assistant: Remote attackers can execute arbitrary code via memory corruption.
- Microsoft Windows Live (MSN) Messenger: Remote attackers are allowed to control the Messenger application, “change state,” obtain contact information and establish audio or video connections without notification.
See Bit9’s full report (.pdf) for information on how the list was put together, including criteria for inclusion.
Source: ZDnet Blog
Chinese Scammers now using Toyota
I received the below email recently and today i received it on my another email address too. So, i thought of putting it here and sharing it with you guys.
TOYOTA INTERNATIONAL LOTTO (HEADQUARTERS)
Customer Service Department Affiliate of Toyota Japan.
#28 Kanashiwa road Tokyo JP
We are pleased to inform you of the announcement made today, You are among the winners of the TOYOTA CAR INTERNATIONAL PROMOTION PROGRAM participants were selected through a computer ballot system drawn from 2,500,000 email addresses of individuals and companies from all part of the world as part of our electronic business Promotions Program.
As a result of your visiting various websites we are running the E-business promotions for. You/Your Company email address, attached to ticket number 719-226-1319, with serial number 902-66 drew the lucky numbers 5, 12, 30, 11, 17, 43 and Bonus number 12 , Your INSURANCE Number: FLS433/ 453L /GMSA, Batch No:- BN-543-ERE343CN and consequently you won in the Second Category of the TOYOTA FORTUNE LOTTO DRAW.
You have therefore been approved for the payment of the sum of US$2,000,000. 00 in cash, including a Toyota car which is the winning present /amount for the Second category winners. This is from the total prize money of US$12,650,000.00 shared among the international winners in the Second category.
CONGRATULATIONS!!!
Please be informed that your won fund of the sum of US$2,000,000.00 is now with the payee center. Contact our agent and give them your full names so that they will re-insure your winning fund under your full names. Together with the port where your winning car should be shipped to.
To begin your claim, please call our claim agent or send email immediately to:-
Certificate Agent, Toyota Email Lotto
Dr.Wong
(TOYOTA CLAIMING AGENT)
Email:dr_wong@live.com
Email:toyotalotterypromo@yahoo.cn
Telephone: 0086:13556070964
www.toyota.cn
NOTE: In order to avoid unnecessary delays and complications, Please quote your
1. Full name
2. Address / contact number
3. Country of origin
4. Age
5. Occupation
6. Tel/fax.
7.Amount deposited.
Kindly contact our customers service center for any assistance on the processing of your claim agent for any complain.
Sincerely ,
Mrs. Ing Chunny Liu
Hon Online Coordinator
I received this email from yahoo.cn domains and one of the address was toyotalotterypromo@yahoo.cn.
I would suggest all my readers to be careful and use little bit of common sense with such emails. We live in the world where nobody gives nothing for free. Please ensure you don't give out any of your personal information to such scams and delete it straight away.
Friday, December 12, 2008
IE7 exploit is already in circulation
They are several reports of exploits circulating in the wild targeting a 0-day vulnerability in Microsoft Internet Explorer 7. These exploits are being used to install malware on Windows systems when unsuspecting users visit websites that have been compromised to host the exploit code.
This vulnerability was first made public in Chinese language discussion forums on or about December 7th, 2008 by a group calling itself the Knownsec team.
Microsoft Security Bulletin MS08-073 (Cumulative Security Update for Internet Explorer, KB958215) released on December 9th, 2008 as part of Microsoft's normally scheduled December security updates does not contain a fix for this vulnerability.
Initial reports by other security vendors mentioned a malformed XML tag as the possible cause of the vulnerability; however, from a deeper analysis it seems that the problem affects the XML parsing engine of IE7 and the library MSHTML.DLL. The vulnerability depends on how certain elements of HTML pages are terminated and therefore could potentially affect not only XML, but also other objects handled by the browser. This means that attackers may start using different attack vectors in the future to exploit this vulnerability, but at the moment it seems that this recent exploit, which has been publicly released on several Chinese forums, only uses the XML elements and tags.
Because of the nature of this attack, it does not depend by any specific ActiveX control, so this time I can’t tell you to disable or set the KillBit for a specific CLSID. However, the attack still requires some JavaScript in order to use heap-spray techniques to achieve a reliable code execution; so, blocking JavaScript for un-trusted websites could help to somewhat mitigate the risk.
At the moment, Many attacks are traced back to Chinese domains and websites, which are used by the exploit to install and download additional malicious code components. The downloaded malicious code is a variety of Downloader, Infostealer, and W32.SillyDC variants. We also recommend blocking the following hosts at network boundaries:
• wwwwyyyyy.cn
• sllwrnm5.cn
• baikec.cn
• oiuytr.net
• laoyang4.cn
• cc4y7.cn
My advice for Windows users is as follows:
• Update your AV and IPS software with the latest signatures
• Run Internet Explorer with limited privileges
• Enable DEP protection for browsers
• Disable JavaScript in Internet Explorer
• Avoid following links to un-trusted sites
Tuesday, December 9, 2008
Top 10 Things To Look Forward To In Windows 7
Web site Windows 7 Centre reports that Microsoft's forthcoming update to Vista, Windows 7, will release its first official beta on January 13, 2009. In meanwhile I did some research to find out Windows 7's awesome new features.
Note: The Windows 7 Preview is a pre-beta release, which means it's not even close to feature-complete. Chances are good that later releases will add or take away features listed below (though most likely later releases will grow these seeds and add a few more goodies).
Second note: Surely Windows 7 includes stability and performance improvements under the hood with highly technical explanations that would make operating system coders very happy. However, this list is purely from my experience as a regular user, living and working with Windows 7 for about five days. Here are just a few of the things to look forward to in Windows 7.
10. Ding-dong, the Sidebar is dead.
One of the first things I hunted down and killed in Windows Vista was the Sidebar, which loaded by default and docked Vista's Gadgets to the right side of your desktop. In Windows 7, the sidebar is no more, and gadgets, should you want them, can roam free across the desktop. This time around, the gadgets feel less distracting to me—the CPU meter and calendar gadgets are my favourites, though this screenshot shows many more.

9. Calculator, WordPad, and Paint got overhauled.
It sucks that Windows 7 is stripping the built-in Photo Gallery and movie-making software that you'll find in Vista (even the Windows Calendar is nowhere to be found in the 7 Preview), but a few of their built-in stalwarts did get some attention. WordPad and Paint both got the Office 2007 ribbon installed, and Calculator now incorporates real world uses into it. At this point only masochists still use Paint and WordPad, but the extension of the ribbon to those inconsequential programs may be a harbinger for more upgrades and ribbon appearances in the future.
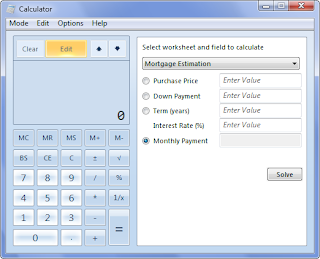
8. Windows 7 will run longer on your notebook's battery power.
While I'm running the Windows 7 Preview on a plugged-in desktop computer, notebook owners will be thrilled to know that Windows 7 promises to run more efficiently and thus longer on battery. It can also identify what's causing battery issues, though this is currently a well-buried option.
7. You can switch between Wi-Fi networks in one click from the system tray.
File this under "a small change can make a huge difference": Click on the Wi-Fi adaptor in your system tray to pop up a menu of available wireless networks. From there you can refresh the list, and choose the one you want to connect to in one click. Another boon for roaming notebook users.

6. You can decide what you do and don't want to see in the system tray.
No more registry-editing to blanket-disable balloon notifications in your system tray! Windows 7 lets you set what icons and notifications you see in your tray with a detailed dialog box. Just right-click the system tray and choose "Customize..." in the menu.

5. You get more control of User Account Control.
The single biggest complaint about Windows Vista was its User Account Control's incessant, nagging, pop-up dialogs that would ask you if you were ABSOLUTELY SURE you wanted to do the thing you just told the computer to do. In the name of security, Vista would even check if this STRANGE and SCARY program called Notepad was ok to run:
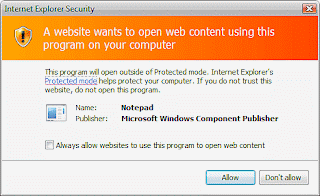
While legions of Vista users would sacrifice the well-intentioned security that User Account Control offered by turning it off completely just to get their sanity back, in Windows 7 you can fine-tune the level of nags, warnings, and confirmation prompts you get.
4. Libraries group similar content; Homegroups to make sharing libraries easier.
Windows networking is a pain in the ass, but Windows 7 is out to fix that with two things: content Libraries and Homegroups. Libraries are a way to group similar types of files even if they live in different folders. For instance, your Video library could include your TV folder, Movies folder, DVD Rips folder, and your Home Movies folder. Then, you can create a Homegroup (basically a reworking of Windows' existing Workgroups), that makes sharing those libraries between PCs easier.
Since I don't have two Windows 7 boxes available, I wasn't able to test how much easier sharing files was between the machines; however, the whole file-sharing layout and UI looks significantly more intuitive for regular Jolenes who just want to view the photos stored on the office computer in the living room.
3. You can instantly snap your windows to size, and clear the desktop in one motion.
As widescreen monitors become more common, easier side-by-side window management is key—and Windows 7 builds that in. While not as configurable as a third-party program like GridMove, Windows 7 offers the ability to snap a window to half your screen size simply by dragging it to the left or right of the screen. Here's what it looks like when you do so—let go of your mouse button and that Lifehacker browser window would snap that half-screen-sized glass overlay you see behind it. Along similar lines, the new "Aero Shake" feature lets you clear the desktop of all background windows by grabbing the top bar of the active window and moving it back and forth quickly.
2. Windows 7 starts up faster.
Scheduling your morning coffee run for the time between the moment you hit the power button on your PC and actually start working sucks. Windows Vista is sloooooow when it comes to starting up and getting you to your desktop; but even the Preview tester release of Windows 7 shows 20% faster boot times than Vista.
1. You can do MUCH more from the Windows 7 taskbar.
Most people live with the Windows taskbar visible on their desktop at all times, so the more use you can get out of the real estate it hogs, the better. Windows 7's taskbar is greatly improved in two ways. First, you can pin programs to it indefinitely for easy quick launch, similar to RocketDock or the Mac OS X dock. Second, on a crowded desktop covered with windows, using the new "Aero Peek" feature, you can preview individual windows from grouped taskbar apps, and even close documents from the thumbnails themselves.
This doesn't sound like a big deal in theory, but in practice when you've got two monitors and a dozen windows open from four apps, Peek comes in way handy. Here's a screencast of Peek in action. There's also a permanent "Show Desktop" button on the far right of the taskbar which both clears the Desktop of all windows (instant Boss button!) and restores them right to where they were in another click. As you can see, Windows 7 is a big pile of small improvements over Vista that amount to a lot in aggregate.
Any other Preview release testers out there unearth features I didn't mention here? Shout 'em out in the comments.
(Note: The Windows 7 Preview's version of Peek is yet incomplete; this is just the beginning of what you'll be able to do with it.)
Monday, December 8, 2008
Online Banking Security
If you're ever online, the chances are good that you access Internet banking services (83% of Internet users in Australia do, according to Sensis). And because it's your money that's involved, you know that security is important. However, there are plenty of myths and misconceptions surrounding Internet banking security. Read on to learn where the risks are.
Myth: Phishing is the biggest banking security risk
Your junk mail folder is doubtless filled with spurious messages asking you to confirm the details of accounts you've never held. Given the prevalence of these phishing attempts, it's easy to assume that fake email is the online bank thief's favourite weapon. However, while these messages certainly should be treated with suspicion and promptly deleted, they're no longer the main attack method for criminals. "Criminals are going to do away with phishing," said Chia Wing Fei, security response manager for security software developer F-Secure's APAC security labs, during a media briefing on security trends. "People are not going to fall for them anymore." The favoured approach is now "drive-by downloads": injecting malicious code into popular web sites in order to infect users. The randomness of phishing attacks is also being replaced with much more sophisticated techniques. "In their attacks, they have metrics built in," Fei said. "They have excellent analysis capabilities in terms of which trojan is effective against which bank.
Myth: Australian banks are too small to be worth attacking
The endless phishing messages for European and American banks might leave you believing that Australia isn't yet on the criminal radar, but that's far from the truth. An analysis of 2300 banking-specific trojans by F-Secure found Australia was the sixth-most common target country for attack. The Commonwealth and ANZ were the most common target, followed by NAB, St George and Westpac. Westpac's relatively low position on the list is partially because it uses an on-screen keyboard for entering passwords. While not totally secure, that approach means hackers have tended to ignore it. "Criminals have a real history of picking the lowest-hanging fruit," said Graham Ingram, general manager for national tech security agency AusCERT. "If it's difficult, why bother?"
Myth: Two-factor authentication will keep you totally safe
Two-factor authentication -- needing not only a password, but also a one-time code either generated electronically or sent via SMS -- is an increasingly common element of bank security. It's a useful additional step, but you shouldn't assume it provides total security. "Users can do everything right and still lose their bank account," Fei said. "Two-factor authentication is not a foolproof thing; you won't prevent your bank account from being stolen. It only changes the tactics the bad guys use." There's also a cyclical problem with adding new layers of security. "One of the dilemmas is every time we introduce a counter-measure, we're raising the level of attack," Ingram said. "There is a chasm developing between the people who get it and the people who don't, and the people who don't are really exposed."
Myth: Account details change hands for large sums of money
While there's a large criminal market exchanging bank and credit card details, it isn't purely about cash. According to Fei, the approach used is often one of barter: details of a bank account with $6000 in it might be traded for 30 active PayPal logins, for instance.
Myth: Your credit card is useless without the CVV
Most online stores demand the three-digit code off the back of your credit card as an additional means of verifying you're the owner. However, there's a healthy black market for software which can reverse-engineer the relevant CVV from a given number, Fei said.
All this doesn't mean that criminals are inevitably going to win. Banks are far more alert to electronic security issues than most other organisations. "In many respects, the banks have this well under control," Ingram said. "It's everyone else who doesn't understand the implications. Think of all the government services online. These are more exposed in my personal view than the banks will ever be."
Being aware of your behaviour, and keeping a close eye on your bank balance and credit cards, remains the best defence. Constant alertness is essential, as Fei explains: "Criminals are getting away with this. They don't have anything to lose. Whatever they're doing, the money's really good."
IE8 Beta 2 users still have to use Compatibility View a lot
Microsoft Plans Compatibility View Fix For Internet Explorer 8
One of the major changes in Internet Explorer 8 is that it adheres much more strictly to web standards than past IE releases. That's a welcome and sensible move, but it has resulted in many sites not rendering well, since they have been built to work with the slightly skewed design principles of earlier IE releases. The second beta of IE8 handled this with a 'Compatibility View' button, but Microsoft's internal research suggested that this wasn't quite enough, as a post on its IEBlog explains:
"We saw from the telemetry data that IE8 Beta 2 users still have to use Compatibility View a lot. Looking at our instrumentation, there were high-volume sites like facebook.com, myspace.com, bbc.co.uk, and cnn.com with pages that weren't working for end-users with IE's new standards compliant default. We could also see from our instrumentation that not all IE8 visitors to those sites were clicking the Compatibility View button. So, large groups of people were having a less than great experience because they weren't aware of the manual steps required to make certain sites work."Microsoft's latest solution is to allow users to opt-in to an automatically updated list of popular sites that need compatibility view and have those sites rendered using the older IE7 approach without requiring manual intervention. That feature will be added to the next beta of IE8, due early in 2009 (there's a similar feature already in Opera). This seems like a pretty good interim solution to me; share your take in the comments.
Refer here for more details on Compatibility View Improvements to come in IE8.
Sunday, December 7, 2008
Koobface virus affecting computer through Facebook's user profiles
FACEBOOOK'S120 million users are being targeted by a virus dubbed "Koobface" that uses the social network's messaging system to infect PCs, then tries to gather sensitive information such as credit card numbers.
It is the latest attack by hackers increasingly looking to prey on users of social networking sites.
Koobface spreads by sending notes to friends of someone whose PC has been infected.
The messages, with subject headers like, "You look just awesome in this new movie," direct recipients to a website where they are asked to download what it claims is an update of Adobe's Flash player.
If they download the software, users end up with an infected computer, which then takes users to contaminated sites when they try to use search engines from Google, Yahoo, MSN and Live.com, according McAfee.
McAfee warned in a blog entry that its researchers had discovered that Koobface was making the rounds on Facebook.
Facebook requires senders of messages within the network to be members and hides user data from people who do not have accounts, said Chris Boyd, a researcher with FaceTime Security Labs.
Because of that, users tend to be far less suspicious of messages they receive in the network.
"People tend to let their guard down. They think you've got to log in with an account, so there is no way that worms and other viruses could infect them," Mr Boyd said.
Privately held Facebook has told members to delete contaminated e-mails and has posted directions at www.facebook.com/security on how to clean infected computers.
McAfee has not yet identified the perpetrators behind Koobface, who are improving the malicious software behind the virus in a bid to outsmart security at Facebook and MySpace.
"The people behind it are updating it, refining it, adding new functionalities," said Mr Schmugar said.
My advise to all of my readers, please be careful out there and make sure you don't click on any videos on Facebook. If you do then don't install any activex or update anything get prompt.
Friday, December 5, 2008
Enjoy Free Solaris 10 OS Training from SUN
In this economic climate, it is as important as ever to keep your skills up-to-date. Now you can enhance your Solaris 10 OS skills with free training at the new Sun Open Learning Center.
The Sun Open Learning Center allows you to:
* Get free access to our most popular Solaris 10 OS training
* Engage in live conversations with Solaris instructors and experts in Second Life virtual world
* Obtain highly desired system administration skills for the Solaris 10 OS
Excellent initiative from SUN. I don't use Solaris much in my daily work life but all the administrators out there should take advantage of this cool offer.
Thursday, December 4, 2008
Facebook Users - Don't click on any link unless you are sure!
FACEBOOK users are under attack again from a virus sweeping through the online social network.
The virus is technically a trojan worm that disguises itself as an email from facebookmail.com.
People are enticed to click on a misspelled video or picture link that directs to a malicious web site.
The title of the dodgy links vary from "Maan,yyou’re great!" to "your ass looks not bad in this video", "Some0ne thinks your special and has a *Hot_Crush* on you. Find out who it could be*" or a youtube link that says '"i can see yooooooooo".
The worm spreads its tentacles by emailing everyone on the victim’s friend list.
According to anti-virus software company Symantec, the trojan works by executing a worm called W32.Koobface.A that searches for cookies on the user’s machine.
If the worm finds the appropriate Facebook cookie, it modifies the users account settings and profile - adding links to malicious sites to trick others into installing the invader.
Facebook discussion boards talk about the trojan directing users to a page which looks like YouTube.
The phoney page asks the user to install a video player upgrade.
Installing the fake upgrade allows the worm to work its magic and access files on the victim’s machine while destroying their Facebook account.
The trojan comes just months after Facebook said it was working to protect its user from phishing scams.
Facebook has begun combating the virus by deactivating link when it can.
Facebook has not released an official comment regarding the attack.
My suggestion would be to all Facebook users to be careful and make sure you don't click any links or watch videos unless you are totally sure about it.
Finally New laws to target ID fraud nationwide in Australia
Draft laws aimed at combatting the fraud, which has been exacerbated by social websites such as Facebook, have been introduced to parliament.
Presently, it is only an offence to steal someone's identity in Queensland and South Australia.
Identity theft across the country will be punishable by up to five years jail.
The crime includes a range of offences including using another person's credit card details to stealing their personal information to open bank accounts and take out loans.
Monday, December 1, 2008
Ebay Scam - Old but still valid and works!
Recently, my good friend Chris Ho, got hit by old eBay scam. He advertised a laptop and was wishing to sell it before Christmas so he can upgrade to a new one.
Unfortunately, the item was won by a international buyer from USA. He received the following email:
From: Raymond Feliciano
Date: Mon, Dec 1, 2008 at 6:27 AM
Subject: I WANT TO PAY NOW FOR #220XXXXXXXX, Sony Vaio Laptop PCG-R505AFT Great Working Order
To: Chris Ho
Dear Seller,
I will like to purchase these Item Sony Vaio Laptop PCG-R505AFT (220XXXXXXX) for a friend oversea as a Christmas gift.He works with British America Tobacco there in West Africa Due to my workload, i might not be able to be checking my mails often.So i will be offering AU $219.00 I want the item posted via Express Post International For Delivery to Him.hope the package will get to him in good condition.. What is the present condition of this item and does it comes in it's original box?.I will be paying you for the item via Bank Deposite, so get back to me with your full name and your bank details where payment will be deliverd to.
MANY THANKS.
Well, I guess this is quite similar to the scam i researched couple of weeks ago on Drive.com - Scammers now targetting Classified websites.
In such scams, buyers send fraudulent checks or send payment by stolen payment accounts. Payment is cleared and sellers usually post the items to different address such as Africa, Kenya, Nigeria etc.
After couple of days or weeks, sellers finds out that payment was made in a fraudulent manner and he has to return the money back to the bank or payment. In this way, sellers looses his item as well as the money.
We can do couple of things to avoid such things:
1) Don't sell anything to international buyers at first place.
2) If you do, make sure safe payment method is accepted such as Western Union, Bank Draft, Bank check from the same country buyer belongs to.
3) Get payment verified by bank before shipping the goods.
4) Use little bit of common sense.
I know these are not the best solutions but at least it will help you out little bit.
Thursday, November 20, 2008
My thoughts on Biometrics / Face Recognition
Biometrics are biological authenticators, based on some physical characteristic of the human body. The list of biometric authentication technologies in still growing. Authentication with biometrics has advantages over passwords because a biometric cannot be lost, stolen, forgotten, lent, or forged and is always available, always at hand. Last and this year we saw heaps of laptops coming up with fingerprint reader as standard.
Now some of the Lenovo notebooks are coming with face recognition software, which is actually a reemergence of an old idea. Now that some systems include integrated cameras with much better quality (1.3MP), facial recognition has become much better. In practice this works very well and is extremely fast at recognition.
The included software lets you log onto your Windows account simply by sitting in front of your system. Your face is your password.
Depending on the software used, face recognition uses multiple techniques to identify a person’s face. Some of the more advanced programs use texture mapping in which a person’s skin texture is analyzed and matched. Most however, define nodal points on a person’s face and then use software to mathematically represent those points. Things measured include distance between the eyes, width of the nose, length of the jaw line, or shape of the cheekbones. Together these concatenate a numerical code which is stored in a database for later retrieval.
Biometrics can become a single of failure though. Consider a retail application in which a biometric recognition is linked to a payment scheme:
As one user puts it, "If my credit card fails to register, I can always pull out a second card, but if my fingerprint is not recognized, I have only that one finger." Forgetting a password is a user's fault; failing biometric authentication is not.
Although equipment is improving, there are still false readings. I think biometrics as unique parts of an individual, forgeries are possible. The most famous example was an artificial fingerprint produced by researchers in Japan.
My thoughts are, forgery in biometrics is difficult and uncommon, forgery will be an issue whenever the reward for a false positive is high enough.
Sunday, November 16, 2008
Scammers now targeting Classified websites...
I recently published a advertise on Australia's leading car selling website "Drive" to sell my car. I have sold couple of cars previously using this website and this company has really good selling rate.
I received few enquiries and most of them were "time wasters". After couple of weeks from the date i published my add i received an enquiry, which i found suspicious and thought of doing some research to see "how this scam works" and later on post it on my blog so other readers can protect them self. To start with, i received an enquiry which was like this:
Dear Shoaib Yousuf,
A Drive user has contacted you with a question about your car for sale on Drive.
Hello, My customer is much interested in your advert car. Pls kindly email me back if the car is still available stating it's present condition and your final price. Regards, Frank.L.Kennon Managing Director Leventis Motors Ltd
E-mail: agent_100brian@yahoo.com
Name Brian Anderson
I found this suspicious straight away and started digging about the company "Leventis Motors". I found no relevant information about the company and another point to note is, why managing directory sending an email using yahoo account?
Anyways, i responded to this add stating, yes - it is still available and i am interesting in selling my car for final price $29,000 AUD. (It was advertised for $29,990)
I received the following response:
from Brian Anderson
reply-to agent_100brian@yahoo.com
to Shoaib Yousuf
date Sat, Oct 18, 2008 at 11:27 PM
subject EXPECT MY MAIL.
mailed-by yahoo.com
signed-by yahoo.com
Reply
Hello,
Thanks for your response to my enquiry concerning your car.
Note that my client who resides here in London wants to conclude this transaction as soon as possible since he wants the vehicle as a present for his son who is resident in South Africa. So the car will be shipped to South Africa and my client bears responsibility for shipment.
Kindly exercise a little patience while i discuss your final price of $29,000 au and other necessary details with my client and also evaluate the on-line photos of the vehicle in question.I will get back to you later today or on Monday morning.
Brian Anderson.
Yeah right, car will be shipped to South Africa and "dad" will send me money from London. I don't need to think twice or guess where this is leading to, I find it quite interesting so i continued to play around with this bit more. So, i responded stating, "sounds like a plan and i would wait for your response as soon as possible". Guess what?, I received an email on Monday morning and it was:
from Brian Anderson
reply-to agent_100brian@yahoo.com
to Shoaib Yousuf
date Tue, Oct 21, 2008 at 12:04 AM
subject CONFIRM PAYMENT AND PICKUP ARRANGEMENT TODAY.
mailed-by yahoo.com
signed-by yahoo.com
Reply
Hello,
This is to inform you that my client has instructed me to proceed with the purchase of your car for his son. He said that I should inform you that the payment will get to you in an Australian bank cheque of ($36,900 AU) which is a refund payment of a cancelled order earlier made by him.
He informed me that he intends using the refund payment to pay for your vehicle.
He further explained that this bank cheque has to be made out in this amount($36,900 AU) to you because company policy only allows a refund payment on one bank cheque.So you are required to deduct cost of your car ($29,000 AU) when the payment gets to you and refund the balance of ($7,900 AU) to my client's agent via western union or moneygram international money transfer for the agent to be able to offset shipping /pickup charges ,contract fees for the pickup agent, taxes, commission and other handling bills.
After payment has reached you and balance is sent back to his agent,the agent will contact the pickup agent who will come for the pick up of the vehicle for shipping to my client's son.
My client is making some necessary arrangement with some shippers and will provide me with the pickup/test driver agent as soon as he decides the agent to contract for the pickup of the vehicle from it's present location.
NOTE: He also instructed that you are to deduct the transfer charges from the remaining balance($7,900 AU) which you will be sending down to his agent via western union or moneygram international wire transfer.
Confirm this whole arrangement and provide the details requested below for payment to be delivered to you.
PAYMENT INFORMATION:
1.YOUR LEGAL NAME IN FULL.........
2.POSTAL ADDRESS IN FULL..........................
3.PHONE NUMBER(S).................
Okay, if anybody use little bit of common sense they will understand that this is all bullshit and scam. Believe me, many people "Don't use their common sense" and still get victim of such scams.
Interesting part is not finished here, i went ahead and provided them with "fake details but real P O BOX details" and "prepaid sim" number.
Take another Guess? Surprise, i received a call from someone with Italian accent saying he has shipped me a cheque and when i will be able to send them money?
Anyways, now it was waiting period. I received a cheque after 3 weeks and i was right. It was shipped from Italy. You guys, won't believe the cheque was of "American Bank - JP Morgan".
I contacted my local bank and used my contacts to find out more details about the cheque. I didn't got much information so i contacted "J P morgan" local Representatives in Melbourne and found the cheque is real but fraudulently honoured. I informed them to take appropriate measures and make sure account holder in informed.
Now, let me tell you guys using my experience, what usually happens after this. Cheque get honoured, person get the money and as per agreement seller sent $7900 via Western Union. After few weeks or months, bank informs seller, "Sorry mate, that cheque was fraudulent" Please refund all the money back.
Bank gets their money back, scammer gets their money and account holder doesn't loose anything. In fact, seller looses $7,900 and still car is on the market or probably sellers sells the car to pay off the bank.
So - Please, i repeat PLEASE use your little common sense and be-aware of these scammers. They will try to scam you in all possible ways.
Friday, November 14, 2008
Patch your Flash player ASAP!
For the second time in two days, Adobe Systems Inc. has warned users of multiple vulnerabilities in one of its most-popular programs and issued a security update to plug the holes.
Wednesday's update was the fourth patch job on the ubiquitous Flash Player this year, and followed by one day an even larger collection of fixes for Adobe Reader, the Web's default PDF application.
The Flash Player update addressed six bugs in Version 9.0.124.0 that run the range from cross-site scripting and information disclosure vulnerabilities to flaws that could be used to inject malicious HTML code in Web sites and launch "DNS rebinding" attacks.
Goto adobe.com to update your flash player or follow the promts from auto-update.
Tor - How it works?
Tor is a software project that helps you defend against traffic analysis, a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security. Tor protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, and it prevents the sites you visit from learning your physical location.
It is a security tool that permits anonymous Web surfing. While it's a tool that can be used both by white hats and gray hats alike, all information security pros should be aware of how it works.
In this screencast, Peter Giannoulis of The Academy.ca details how Tor can be used by individuals to ensure their surfing habits aren't recorded by malicious hackers, and how IT professionals involved in auditing networks can mask their location so that a more thorough audit can be conducted.
Refer here to watch video by SearchSecurity.
Gmail - a new voice and video chat plug-in
GOOGLE IS EXCITEDLY announcing its latest mission to gain a bigger user count for its Gmail service – a new voice and video chat plug-in.
So far Google has been slowly creeping alongside the likes of other email giants including Microsoft Live which has 283 million users and Yahoo mail which is just slightly behind with 274 million.
Gmail was seemingly stuck in third place with just 113 million users, which is why it has come up with this new video and voice chat service which will come free as part of the Gmail package. Although both of Google’s main competitors also offer a video and chat service, it is not integrated into the mail section like Gmail’s is – which makes it marginally different.
*****Not security related*****
Thursday, November 13, 2008
Malicious Worm That Attacks Social Networks
PandaLabs has recently detected a new variant of the Boface family that affects the social networks Facebook and MySpace. In this case, the worm sends all the user's friends a message which contains a link to a supposed YouTube video.
In order to view the video, the user is required to download a Flash Player update. However, the downloaded file is not an update but a copy of the worm.
This shows that cyber-crooks are still interested in the social networks to distribute their creations. In fact, Facebook and MySpace with millions of registered users have become a profitable target for them.
Facebook has started taking measures to solve this problem. You can check it here.
Tuesday, November 11, 2008
4,000 Viruses in a month? Are we all using Anti-Virus?
Up to 3,910 new types of computer viruses were recorded in Vietnam in October, including 3,905 of international origin and 5 of domestic origin.
According to the leading networks security agency in Vietnam, BKIS Network Security Centre, the bugs attacked more than 6.2 million computers in Vietnam during October. The most popular virus is X97M.XFSic, which infected over 73,000 computers.
BKIS said in October, 50 websites of Vietnamese companies and agencies were hacked. Of them, 24 sites were attacked by Vietnamese hackers and 26 by foreign hackers. BKIS also unveiled serious errors in websites of 11 businesses and government agencies.
According to BKIS, there is a new method of infection for virus to affect computers, which has swindle anti-virus software and resulted in the loss of standard files of the operating system. The users, thus, have to reset the whole system.
BKIS counted 92 new types of viruses which employed this way of infection and they attacked 41,600 computers in Vietnam.
All I can say, we need to make sure, we are using up to date anti-virus to protect ourselves from all these up coming threats plus make sure we are regularly backing up our data.
Kaminsky cache poisoning flaw
One in four public-facing domain name system (DNS) servers on the internet are still vulnerable to the Kaminsky flaw, according to the fourth annual survey of DNS servers by network services vendor Infoblox.
The flaw allows hackers to sabotage DNS servers and send web users to sites set up to hack into their systems. Cricket Liu, architecture vice president at Infoblox, explained that the survey used the same tests as last year, but added a check on whether servers had patched against the Kaminsky flaw by performing source port randomisation.
"The number of name servers out there has increased slightly from 11.7 to 11.9 million, and firms are using more secure up-to-date versions of the Berkeley Internet Name Daemon package," he said.
Refer here to read full article.
Wednesday, November 5, 2008
Facebook and Privacy
I have blogged heaps of time about Facebook issues. I know, I have facebook account myself. I don’t want people to stop using Facebook or close their account in fact I would like them to be aware of all the possible security issues and treats available out there.
In the past, I have blogged about spammers are using facebook account to spam, spreading malware and social engineering. I advice my readers to make sure they really know the people they are adding and not to give out un-necessary information which can be used by someone to steal your identity or to harass you.
After 1 year on Facebook, I posted my picture couple of days ago. Several people and my friends asked me to upload a picture. I always refused to do so.
Let me tell you the reasons why I personally didn’t upload the picture.
1) My picture can be copied by anyone.
2)I have open profile because I am always looking to make contacts and friends. I tend to be bit reluctant to make sure what information I give to them.
Now I have uploaded my picture (just one), reason is;
1) My picture can be copied from my blogger profile anyway so there is no protection and I realize now that facebook friends can also see my picture from my profile if they are not visiting my blog.
2) I have uploaded only one picture though and that is also of “me alone” not with anyone else.
Okay, let me come to point. I have been investigating this particular "privacy issues with Facebook" for last couple of weeks. I will try to sum up my findings and concerns,
Consider this scenario:
I have a friend whose name is “Alisha” and she is added in my facebook friends list. She has a friend whose name is “Sarah”. I like her and I want to get her details but I notice her profile is restricted to her friends only. I sent a request to her but unfortunately she has not responded yet.
Suddenly, “Sarah” uploaded few photos of her friends and tagged “Alisha” in those photos. As soon, she tagged “Alisha” I was able to see all her photos in that particular album plus I was able to see her profile too. I found out more details and bingo I was able to harass her.
Now, consider another scenario:
I have my work friends, my family and my other friends in my facebook friend list. One of my friends uploaded a picture tagging me which is quite personal. As soon he tagged me, all my family members, my work colleagues and my other friends were able to see my personal picture plus all the pictures in that particular album.
Consider third scenario:
I have my neighbour added in my account as a friend. He uploaded few pictures in his profile of the party he had at his home. I commented on his photos and guess what my other friends see:
"Shoaib Yousuf commented on XYZ's picture"
Any of my friends can see my neighbours picture and infact his profile too. After commenting on his picture, i am really not giving any privacy to his personal party pictures.
So – what we learned from this?
Facebook is good social network tool but it doesn’t offer security or privacy what so ever. I suggest and advice all my readers to make sure if they upload pictures don’t tag them. If they still want to do, make sure you select the appropriate security permissions so all other people from your friend’s friend list cannot view it.
If you have any questions, suggestions or your past experience you would like to share let me know.
Thursday, October 30, 2008
Scan your system with 8 different anti-malware applications
Free application Hitman Pro scans your system for malware using not one, not two, but eight different anti-malware applications. Essentially, Hitman Pro is a helper utility that runs up to eight different cleaning tools when you tell it to. Some are favourites we all know and love, like Ad-Aware and Spybot S&D, while others are a bit more obscure. The idea behind Hitman Pro is that you've got a one-stop shop for killing off any malware that hits your system—regardless of whether it's spyware, adware, or some nasty virus. As the MakeUseOf post points out, scanning your system with each app can be a time-consuming process, so it's best to use when your computer is idle.

Refer here to download and for more details.
Microsoft NT Hash cracker from LM Password
lm2ntcrack provides a simple way to crack instantly Microsoft Windows NT Hash (MD4) when the LM Password is known. lm2ntcrack is Free and Open Source software. This sofware is entirely written in Perl, so its easily ported and installed.
lm2ntcrack must be used with the password cracker John the Ripper.
Please refer here for more details.
Tuesday, October 28, 2008
Squirtle
The purpose of this little doodad is to help you prove to your employer, your client, your best friend, your dog, or God that NTLM is truly dead. It does this by taking control of any browser that comes into contact with it and making it perform NTLM authentication at will. By using a set of API calls you can imbed Squirtle into existing penetration toolkits, proxies or otherfun tools at your disposal.
Please refer here for more details and to download.
pyrit - A tool to estimate the real-world security
Pyrit takes a step ahead in attacking WPA-PSK and WPA2-PSK, the protocol that today de-facto protects public WIFI-airspace. The project's goal is to estimate the real-world security provided by these protocols. Pyrit does not provide binary files or wordlists and does not encourage anyone to participate or engage in any harmful activity. This is a research project, not a cracking tool.
Pyrit's implementation allows to create massive databases, pre-computing part of the WPA/WPA2-PSK authentication phase in a space-time-tradeoff. The performance gain for real-world-attacks is in the range of three orders of magnitude which urges for re-consideration of the protocol's security. Exploiting the computational power of GPUs, this is currently by far the most powerful attack against one of the world's most used security-protocols.
Pyrit compiles and runs fine on Linux and MacOS X. None of the BSD systems were tested but all posix systems should be fine anyway. I don't care about Windows; drop me a line (read: patch) if you make Pyrit work without copying half of GNU in binary form...
Refer here to read more details and to download or refer here to read their blog.
Sunday, October 26, 2008
Emergency Patch released by Microsoft
Microsoft fixed a critical bug in its Windows operating system Thursday, saying that it is being exploited by online criminals and that it could eventually be used in a widespread "worm" attack.
Microsoft took the unusual step of issuing an emergency patch for the flaw, several weeks ahead of its regularly scheduled November security updates, saying that it is being exploited in "limited targeted attacks."
Please refer here to read full article on CIO.
I quote from Microsoft's Security Vulnerability Research & Defense website:
Most perimeter firewalls will block exploit attempts from outside your organization
If you are behind a perimeter firewall that filters inbound connections to TCP ports 139 and 445, you will not be reachable from the Internet. This is a common home user scenario. In this scenario, only the machines in your local LAN will have the ability to exploit this vulnerability.
This basically means, if you have strong filtration at firewall you are still safe from this exploit but this doesn't mean we should take vulnerability easy. I recommend all my readers and especially home users to deploy this patch as soon as possible.
More useful links can be found on Roger Halbheer's blog.
Hackers Use Nvidia Graphics Card to Smash WPA2 10,000 Percent Faster
Global Secure Systems has said that a Russian's firm's use of the latest NVidia graphics cards to accelerate WiFi ‘password recovery' times by up to an astonishing 10,000 per cent proves that WiFi's WPA and WPA2 encryption systems are no longer enough to protect wireless data.
David Hobson, managing director of GSS, claimed that companies can no longer view standards-based WiFi transmission as sufficiently secure against eavesdropping to be used with impunity. He also said that the use of VPNs is arguably now mandatory for companies wanting to comply with the Data Protection Act.
He said: “This breakthrough in brute force decryption of WiFi signals by Elcomsoft confirms our observations that firms can no longer rely on standards-based security to protect their data. As a result, we now advise clients using WiFi in their offices to move on up to a VPN encryption system as well.
Please refer here to read full article.
WPA and WPA2 is the secure method after WEP which is commonly used by home users and perhaps many small-to-large size companies. This basically means, all wireless users using WPA and WPA2 are at risk and we should start looking at more secure wireless methods before we get victim of these types of attacks.
Thursday, October 23, 2008
ARPWatch
Arpwatch tool monitors ethernet or fddi activity and maintain a database of ethernet/ip address pairings. It also reports certain changes via email. Arpwatch uses libpcap, a system-independent interface for user-level packet capture. Before building arpwatch, you must first retrieve and build libpcap. Once libpcap is built (either install it or make sure arpwatch and libpcap share the same parent directory), you can build arpwatch using
the procedure in the INSTALL file.
Refer here for more details and more interesting tools.
Active Reconnaissance network security tool
Firewalk is an active reconnaissance network security tool that attempts to determine what layer 4 protocols a given IP forwarding device will pass. Firewalk works by sending out TCP or UDP packets with a TTL one greater than the targeted gateway.
If the gateway allows the traffic, it will forward the packets to the next hop where they will expire and elicit an ICMP_TIME_EXCEEDED message. If the gateway hostdoes not allow the traffic, it will likely drop the packets on the floor and we will see no response.
To get the correct IP TTL that will result in expired packets one beyond the gateway we need to ramp up hop-counts. We do this in the same manner that traceroute works. Once we have the gateway hopcount (at that point the scan is said to be `bound`) we can begin our scan.
It is significant to note the fact that the ultimate destination host does not have to be reached. It just needs to be somewhere downstream, on the other side of the gateway, from the scanning host.
To read more details about Firewalk please refer here.
Data breaches are common in Australia
A new survey reveals almost 80% of local companies have experienced data breaches in the past five years, with 40% recording between six and 20 breaches.
The Symantec Australian data loss survey shows 59% of businesses suspect they have been the victim of data breaches, but are unable to identify stolen information. A whopping 34% of respondents report an average breach cost them $5000, while 14% say breaches cost them between $100,000 and $999,999, and 7% over $1 million.
But the main cause of data breaches, the survey reports, was lost laptops at 45%, while human error accounted for 42% of cases. Malicious attacks were responsible for 28% of breaches, while hacking and malware were responsible for 24%.